Imagine being able to interact with your database just like you would with a human. In this section, we will explore the concept of conversing with databases, where you can pose questions in everyday language and receive insightful answers directly from the data.
🧩 Deterministic vs Generative Models
Let’s start by discussing these concepts, as they will be essential for understanding the rest of the topic.
In simple terms, deterministic models follow strict rules to give you the same result every time you input the same data. They are predictable, like solving a math problem with a formula. Generative models, on the other hand, are more flexible. They use patterns in data to create new possibilities, so their results can vary, even with the same input. Think of them like having a conversation—responses may change depending on how the context is interpreted.
📝 Text-to-SQL Models
Text-to-SQL models represent the most intuitive and straightforward application of generative models for database querying. This approach requires minimal effort for implementation: we simply pass the user’s message to the model along with information about the database structure, and in return, we receive an SQL command to execute. However, this implementation is not without its challenges; current the best text-to-SQL models achieve only about 70% accuracy in generating correct queries. This level of precision is insufficient for a reliable system. To address this, additional techniques are often employed to enhance their effectiveness and safeguard against potential misuse. By combining text-to-SQL capabilities with these strategies, we can build more robust and trustworthy data interaction solutions.
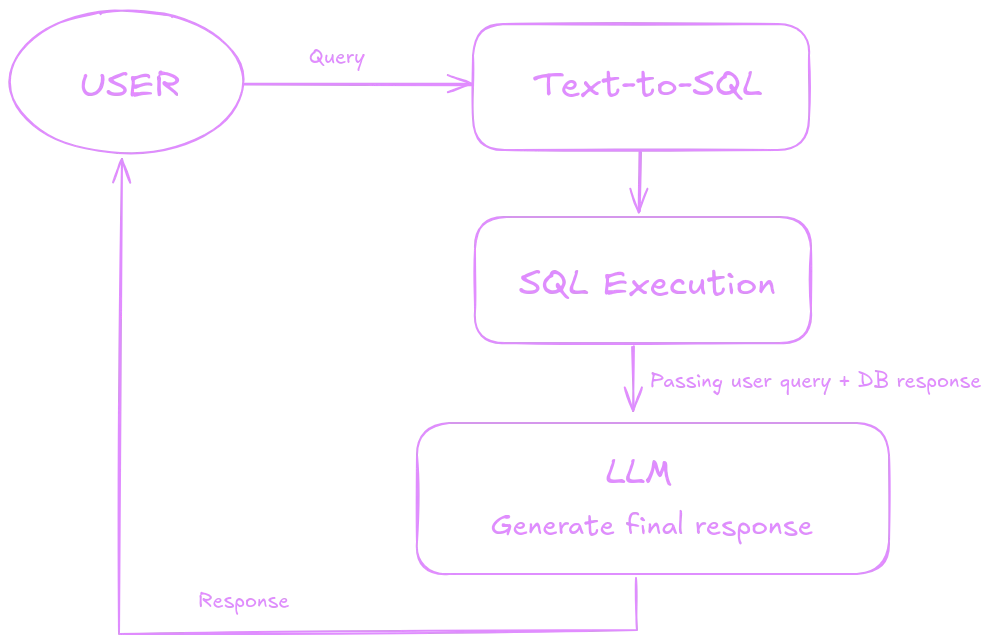
🧠 Domain Knowledge and Security
Think of a text-to-SQL model as a random person on the street. Even if we provide some information about the database structure, they might not fully understand our question because they lack our domain-specific knowledge. One effective way to improve the model’s performance is by supplying it with domain knowledge. This is where embeddings come into play. By creating a knowledge base, we can analyze the user’s query before passing it to the text-to-SQL model and add relevant context or information related to the user’s question. This approach can significantly improve the accuracy of the model’s output.
Another important factor to consider is securing the database to ensure that the model’s operations are read-only (unless we explicitly want otherwise). Depending on the database, this can be managed in various ways, such as by assigning the proper permissions to the database user. These safeguards prevent accidental or malicious changes to the database, helping maintain its integrity and security.
❓ Should LLMs Write SQL?
A less flexible but significantly safer and more predictable approach is to combine deterministic and generative models by providing API endpoints and usage guidelines to the LLM, while designing the API in a traditional manner. In this scenario, we know exactly what the model has access to and how it utilizes that access. The model selects the most suitable option from multiple choices for the current task and invokes a specific endpoint that returns the appropriate data. This means that the model does not have direct access to the database, ensuring enhanced security and control over the data interactions.

🔗 Generative Models & Traditional Database Systems
While generative models like text-to-SQL provide an exciting and intuitive way to interact with databases, they don’t have to replace traditional database systems entirely. A powerful approach is to combine the strengths of generative models with the precision and reliability of classical database querying. By integrating LLMs with traditional systems, we can build hybrid solutions that allow users to ask natural language questions while leveraging the robust data management features of existing databases.
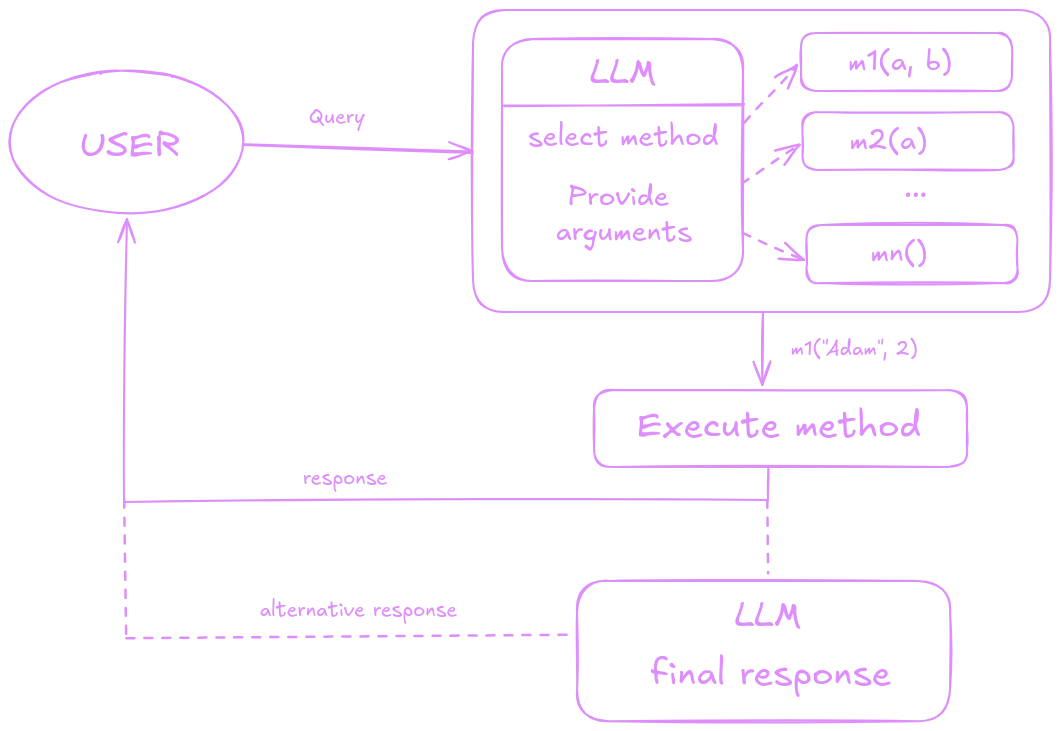
In this model, LLMs can assist by generating initial queries, providing recommendations, or offering context, while the final query execution and data retrieval are handled by traditional systems. This synergy allows for greater flexibility and ensures higher accuracy and security, benefiting from the best of both worlds.